OK, it’s Friday afternoon, let’s try to answer this.
Yes, there are always secrets - but they do not always have to be passed. The password (something we know) has been with us for a very long time - way before computers.

Even longer, going back to the Roman Army using watchwords.
The problem with secrets? They are hard to keep. Humans cough them up to malicious sites, social engineering, checking them into source code, etc. Even Microsoft has had a bad stretch of not being able to keep tokens a secret lately!
So, the goal is to not to use secrets. The answer, as @Olga pointed out, is to use public key cryptography. In this scenario, the client makes a request to the server. The server sends a random challenge phrase. The client encrypts the challenge with its private key and sends it to the server. The server decrypts the challenge with the clients public key. If they are the same, then we know the client has the private key used upon setup.
Server to server authentication is done with digital certificates. Again, each side has secrets but they are not transmitted. Web certificates are tied to the fully qualified domain name so they cannot be used on other machines even if stolen.
The reason the BFF is useful is you cannot trust a client with others’ secrets.
But Mark, aren’t we just trusting our API server to keep the secret?
Well, we kick the can a little further down the road here. The ideal situation is the secret is not at the server but kept in a vault. In order for the API server to get the secret, there’s a pair of digital certificates that allows the API server to retrieve that secret. The API server will retrieve it each time it needs it. (A better practice would be that the secret gets rotated each time it’s used much like Microsoft does with Local Adminstrator Password Solution - LAPS.) Obviously, one has to balance the risk appetite with the effort. But using a BFF that gets the credentials from secret store is enough juice that’s worth the squeeze.
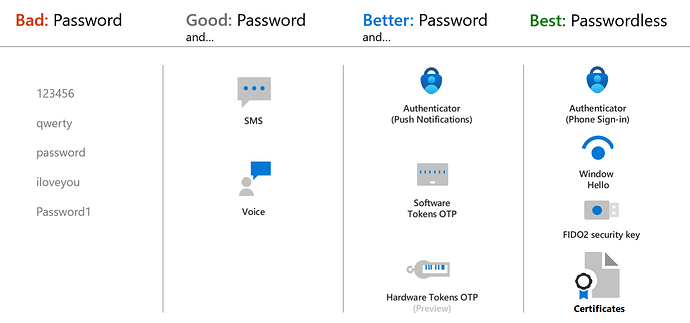
As for humans, here’s some nice weekend reading on how passwordless works for our users by passing challenges across multiple channels while using public key cryptography behind the scenes. No passing around secrets.