Testing 2024.1.13 and a user went to change their password and this popped up:
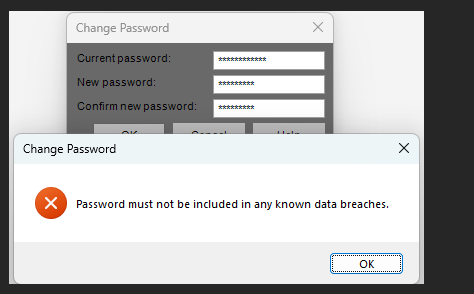
What is Epicor checking against?
Testing 2024.1.13 and a user went to change their password and this popped up:

What is Epicor checking against?
Troy Hunt’s “Have I Been Pwnd” site has both an API and download. The passwords are not stored in the clear but are hashed. You can perform the same hash and check to see if the hash matches a password’s hash that is in a breach.
Not sure if Epicor is using this as there are other services as well.
I think you can disable this in Password Policy Maintenance. Check to see if the “Use advanced password validation” field is ticked. Cloud users are stuck with it enabled however.
Cloud users are fortunate that it’s enabled! Reducing the risk of credential stuffing is not a bad idea.
Have you considered moving to AD auth?
I did check the users email address in You have been Pwnd and it had been breached. Still not sure what Epicor is using.
I did find the new setting in Password maintenance thanks to @Dylan_Ainsworth
@jgehling i would love to get to AD auth but just havn’t taken the time to look into it.