Version 10.X / 202X.Y → 202X.Z
This topic covers tips, tricks and known issues for making the jump between the two above sessions.
Tips:
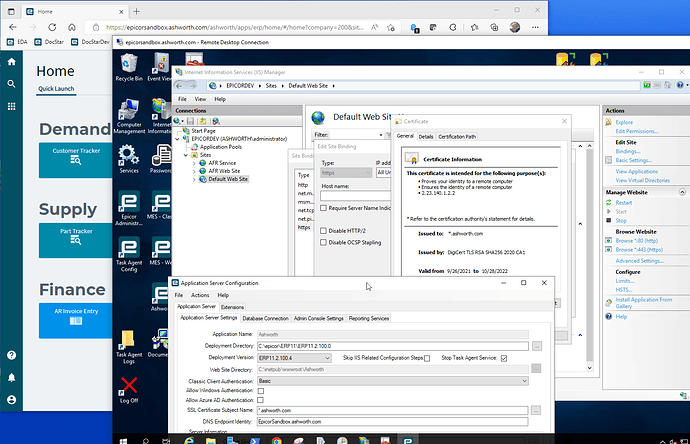
An SSL certificate that isn’t wildcard, used with a net.tcp appserver in 10.2.700, doesn’t seem to be able to satisfy the requirements for 2022. Somewhere there’s a @Bart_Elia comment that there are a lot of endpoints in Kinetic, so maybe that’s why.
Getting a “SPLIT_STRING” Issue on initial login? Check and update the compatibility level in SQL server on the specific user database and make sure it’s 2017 or higher. On a similar note, the WIndows version / SQL server version matches in the upgrade guide are the ONLY ones that work. Make sure you use one of the options listed.
If you have an on-prem setup using RDS / RemoteApps instead of clients, you need a self-signed certificate from your AppServer installed on each TS. You ALSO still need a public certificate if you have anything connecting from outside, like SalesForce making Epicor API calls. In order to make this work, you need the self-signed certificate binding on port 443 WITH server name and the public cert binding separately, WITHOUT server name. This is all assuming the old-fashioned server.domain.local naming convention.
Don’t use IIS to create self-signed certificates - they don’t work with this setup. Use Admin Console to create the certs when you create the AppServers.
If Solution CABs won’t install properly, especially UD fields but even internal objects, make sure you ran Epicor as administrator to install them.
EMWW / EMW / EKW has changed its licensing system. In 10.2.700 there was just a license code to enter. In 2022.1 you have to open a request in EpicCare to “download a copy of a license I already own” and for some reason, that option sometimes doesn’t appear. I had to log out of EpicCare and back in, and there it was. You then import that license into your appservers in EAC.
The version of EMW that works with 10.2 does not work with 2022.1. To upgrade EMW go to downloads.biscit.com and enter your license key to access the downloads area. They recommend using the Play Store instead, but our devices don’t have the play store and aren’t going to. We transfer the APK to the device via bluetooth and tap to install. There are details in the guide on EpicWeb, make sure you follow them especially redoing the setup of DataWedge if you’re using it. Also make sure you uninstall the old EMW version first.
The version of System.Data.SqlClient that ships with Kinetic doesn’t work - it seems to just be a redirect. I don’t think they expect it to be added as a reference in custom code. We were relying on it for custom BPMs and resolved this with the Microsoft.Data.SQLClient. I got the DLL by creating a CMD-based dotnet project, adding the nuget Microsoft.Data.SQLClient package it, and running it. This compiles everything into its folders and I just borrowed the DLL from there. I know it’s hacky.
Known Issues:
Solution workbench has improved 100% lately, but it still doesn’t seem to collect up the RDLs from BAQ Reports.